In brief
On 25 June 2024, the Government proposed to enact a new piece of cybersecurity legislation, tentatively entitled the Protection of Critical Infrastructure (Computer System) Bill (“Bill“), to enhance the protection of computer systems of critical infrastructures (CIs). On 2 July 2024, the proposed legislative framework was tabled to the Legislative Council (LegCo) Panel on Security for consultation. The proposed legislation would require CI operators (CIOs) to fulfill certain statutory obligations and take appropriate measures to strengthen the security of their critical computer systems (CCSs) and minimise the chance of essential services being disrupted or compromised due to cyberattacks. It is proposed that a new Commissioner’s Office is to be established under the Government’s Security Bureau for the implementation of the proposed legislation.
The Government is currently consulting the relevant sectors and plans to introduce the proposed Bill into the LegCo by the end of this year. The enactment of Hong Kong’s first cybersecurity legislation is imminent.
In more detail
Hong Kong does not currently have any cybersecurity legislation in relation to CIs.
The Government first announced the plan to enact a cybersecurity legislation in its 2021 Policy Address. The current recommendations in the proposed legislative framework are in alignment with the areas of focus of the proposed cybersecurity legislation as indicated by the Government previously (see our previous client alert).
In the Asia-Pacific region, the Chinese Mainland, Singapore and Australia, among others, have all passed cybersecurity legislation with CI concepts. Indeed, the proposed legislation will be enacted against the backdrop of the existing cybersecurity framework of the Chinese Mainland, including the Cybersecurity Law 2016 and Regulation for Safe Protection of Critical Information Infrastructure 2021. As the Bill is yet to be published, it is too early to comment on how the Hong Kong legislation will compare to the cybersecurity regulatory regimes of other jurisdictions.
The Government has, however, made clear that only expressly designated CIOs and CCSs will be regulated under the proposed framework.
1. What are considered CIs?
It is proposed that CIs should cover the following two major categories:
- Infrastructures for delivering essential services in Hong Kong, namely energy, information technology, banking and financial services, land transport, air transport, maritime, healthcare services, and communications and broadcasting.
- Other infrastructures for maintaining important societal and economic activities, e.g., major sports and performance venues, research and development parks, etc.
2. What are considered CCSs?
CCSs are only computer systems that are relevant to the provision of essential services or the core functions of computer systems, and those systems which, if interrupted or damaged, will seriously impact the normal functioning of the CIs. This means that other computer systems of the CIOs that are not designated as CCSs will not be subject to the proposed legislation. The requirements of the proposed legislation will apply to all CCSs, whether they are physically located in Hong Kong or not.
The Commissioner’s Office will consult the CIOs on what systems are essential to their operations when considering whether any designation should be made.
3. Who needs to fulfill the statutory obligations?
An organisation-based approach would be adopted and only those operators that have been expressly designated as CIOs will be required to fulfill their statutory obligations under the proposed legislation. The proposed legislation would only set out the names of the essential services sectors instead of disclosing the list of CIOs so as not to create targets for cyberattacks.
4. What are the statutory obligations of CIOs?
The statutory obligations would be imposed on CIOs to ensure that they will put in place a sound management structure to protect the security of CCSs, implement the necessary measures to prevent cyberattacks on these systems, and promptly respond to and recover the affected systems in case of computer system security incidents. The obligations do not extend to the personal data and business information in the systems, however.
The proposed obligations of CIOs are set out below:
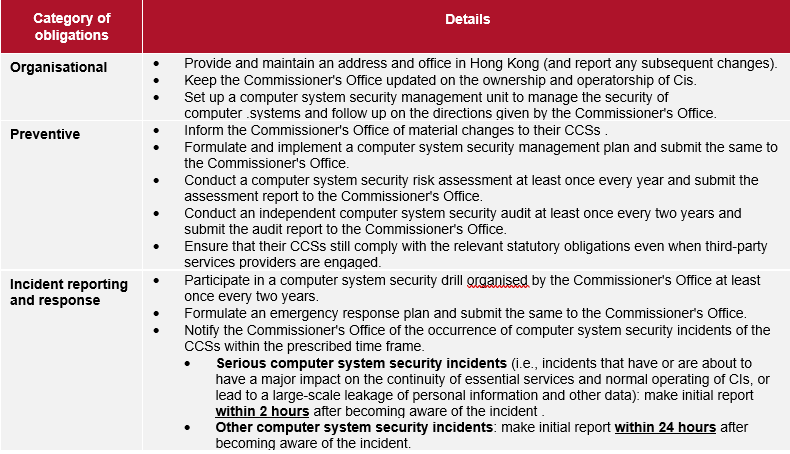
5. What are the functions, duties and powers of the Commissioner’s Office?
The functions and duties of the Commissioner’s Office are:
- Designating CIOs and CCSs.
- Establishing and issuing a “Code of Practice” (CoP) which sets out the proposed standards based on statutory requirements and giving advice to CIOs on the measures to be adopted.
- Monitoring computer system security threats against CCSs.
- Assisting CIOs in responding to computer system security incidents.
- Investigating and following up on non-compliance of CIOs.
- Coordinating with various government departments (e.g., the Office of the Government Chief Information Officer (OGCIO)) in formulating policies and guidelines and handling incidents.
- Issuing written instructions to CIOs to plug potential security loopholes.
The Commissioner’s Office will have extensive investigation powers to investigate security incidents against a CCS and the offences under the legislation. The Secretary for Security would be empowered to specify or amend by way of subsidiary legislation in respect of certain details relating to the powers of the Commissioner’s Office or the statutory obligations of CIOs, e.g., the information that may be required by the Commissioner’s Office from a CIO, and the type of material changes to CCSs that is required to be reported to the Commissioner’s Office.
6. What are designated authorities?
The government proposes to designate certain sector regulators as designated authorities to monitor the discharge of organisational and preventive obligations by the essential services sectors. The following designations are proposed at this stage: the Monetary Authority (HKMA) is to be responsible for regulating some service providers in the banking and financial services sector, while the Communications Authority (CA) is to be responsible for regulating some service providers in the communications and broadcasting sector. Designated authorities may issue relevant guidelines for the institutions regulated.
7. Can CIOs appeal against a decision of the Commissioner’s Office?
An appeal board will be established to allow CIOs to appeal against a CIO or CCS designation or a written direction issued by the Commissioner’s Office.
8. What are the offences and penalties for non-compliance?
The proposed offences include:
- CIOs’ non-compliance with statutory obligations.
- CIOs’ non-compliance with written directions issued by the Commissioner’s Office.
- Non-compliance with requests of the Commissioner’s Office under the statutory power of investigation.
- Non-compliance with requests of the Commissioner’s Office to provide relevant information relating to a CI.
The penalties will only include fines. The level of fines will be determined by the courts, with maximum fines ranging from HKD 500,000 to HKD 5 million. Additional daily fines for persistent non-compliance will be imposed for certain offences.
Please note that if a CIO’s non-compliance with the statutory obligations results from a third-party service provider’s inadequate action, the CIO would still be held responsible for the non-compliance.
9. What will happen next?
The Government is currently consulting with relevant stakeholders on the proposed legislation, and the consultation period should end in August. While relevant stakeholders are / will be approached by the Government, other interested parties may wish to submit their comments and proposals to a member of the LegCo directly, or channel such comments to them through a relevant industry association.
The Government plans to introduce the proposed Bill into the LegCo by the end of this year and aims to set up the Commissioner’s Office within one year following the passage of the proposed Bill, after which the proposed Bill would come into force within six months.
10. Any other areas to watch out for in the proposed Bill?
Given that the details of the proposed legislative scheme are only available in outline form at this juncture, there are several areas in which further clarity would be welcomed in the proposed Bill, and in particular:
- Scope of application: the term “information technology” in the first category of CIs is broad and not defined, whereas the second category of CIs is open-ended. Companies would not always know whether or not they may be suddenly made subject to the proposed legislation, which is not conducive to supporting a well-defined operating environment for businesses.
- Overlapping reporting and compliance obligations: Companies subject to the proposed legislation may have to report incidents to and observe compliance from multiple regulators, including the HKMA and the CA, as well as the Privacy Commissioner for Personal Data (PCPD) where personal data is breached or compromised by an incident affecting a CSS (although reporting a data breach to the PCPD remains voluntary under the Personal Data (Privacy) Ordinance now). There may also be conflicts among different regulators’ directions.
- Omission of operational technology: The proposed legislative framework focuses on “computer systems”, “information technology” and associated cybersecurity risks and concerns, but does not mention operational technology, which is about controlling physical processes, machines and equipment.
- Extent of investigative powers of the Commissioner’s Office: The extent of the Commissioner Office’s power to compel production of documents, etc. will likely not become clear until the Bill is published. In addition, since the Government is not subject to the obligations in the proposed legislation, there may be concerns that CIOs sharing sensitive technical information with the Government will make Government systems more of a target for cyberattacks.
- Emergency response plan: It is not clear whether the obligation of CIOs to submit their emergency response plans entails a mere filing requirement, or will be subject to a review and approval process from the Commissioner’s Office.
If you would like to discuss any of these issues, please get in touch with our team of experts.







